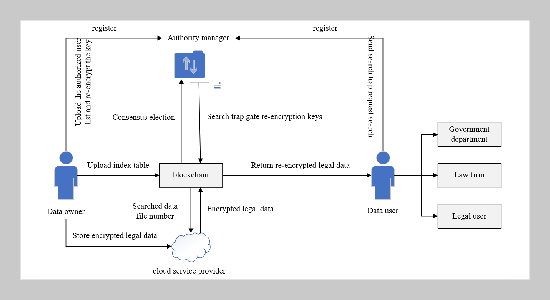
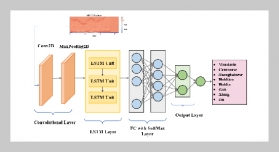
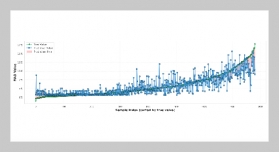
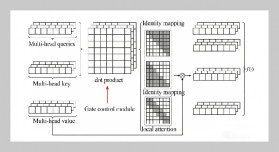
- [1] O.Popoola, M. Rodrigues, J. Marchang, A. Shenfield, A. Ikpehai, and J. Popoola, (2024) “A critical literature review of security and privacy in smart home healthcare schemes adopting IoT & blockchain: problems, challenges and solutions" Blockchain: Research and Applica tions 5(2): 100178. DOI: 10.1016/j.bcra.2023.100178.
- [2] O.Kuznetsov, P. Sernani, L. Romeo, E. Frontoni, and A. Mancini, (2024) “On the integration of artificial in telligence and blockchain technology: a perspective about security" IEEE Access 12: 3881–3897. DOI: 10.1109/ACCESS.2023.3349019.
- [3] S. Yin, H. Li, A. A. Laghari, L. Teng, T. R. Gadekallu, and A. Almadhor, (2024) “FLSN-MVO: Edge Comput ing and Privacy Protection Based on Federated Learn ing Siamese Network With Multi-Verse Optimization Algorithm for Industry 5.0" IEEE Open Journal of the Communications Society: DOI: 10.1109/OJCOMS.2024.3520562.
- [4] V.Raja et al., (2024) “Exploring challenges and solutions in cloud computing: A review of data security and privacy concerns" Journal of Artificial Intelligence General science (JAIGS) ISSN: 3006-4023 4(1): 121–144. DOI: 10.60087/jaigs.v4i1.86.
- [5] O.D.Segun-Falade, O. S. Osundare, W. E. Kedi, P. A. Okeleke, T. I. Ijomah, and O. Y. Abdul-Azeez, (2024) “Assessing the transformative impact of cloud computing on software deployment and management" Computer Science & IT Research Journal 5(8): DOI: 10.51594/csitrj.v5i8.1492.
- [6] Y. Mou, L. Deng, and Y. Ruan, (2025) “A Revocable Certificateless Encryption Scheme for Multi-User" Con currency andComputation:Practice and Experience 37(1): e8321. DOI: 10.1002/cpe.8321.
- [7] S. Yin, H. Li, L. Teng, A. A. Laghari, and V. V. Estrela, (2024) “Attribute-based multiparty searchable encryption model for privacy protection of text data" Multimedia Tools and Applications 83(15): 45881–45902. DOI: 10.1007/s11042-023-16818-4.
- [8] A.Bisht, A.K.Das, and D.Giri,(2024)“Personalhealth record storage and sharing using searchable encryption and blockchain: A comprehensive survey" Security and Privacy 7(2): e351. DOI: 10.1002/spy2.351.
- [9] C. Jiang, C. Xu, and G. Yang. “Device-enhanced se cure cloud storage with keyword searchable encryption and deduplication”. In: European Symposium on Research in Computer Security. Springer. 2024, 396–413. DOI: 10.1007/978-3-031-70903-6_20.
- [10] M. Xie, X. Yang, H. Hong, G. Wei, and Z. Zhang, (2024) “A novel verifiable chinese multi-keyword fuzzy rank searchable encryption scheme in cloud environments" Future Generation Computer Systems 153: 287–300. DOI: 10.1016/j.future.2023.11.017.
- [11] F.Wang, H.Xiao, J.Wang, Y.Wang, and C.Cao,(2024) “Efficient secure channel free identity-based searchable encryption schemes with privacy preserving for cloud storage service" Journal of Systems Architecture 149: 103089. DOI: 10.1016/j.sysarc.2024.103089.
- [12] Z. Lin, H. Li, X. Chen, M. Xiao, and Q. Huang, (2024) “Identity-Based Encryption with Disjunctive, Conjunctive and Range Keyword Search from Lattices" IEEE Trans actions on Information Forensics and Security: DOI: 10.1109/TIFS.2024.3459646.
- [13] H. Liu, L. Deng, Y. Mou, B. Li, and J. Wen, (2024) “Identity-based authenticated multi-keyword searchable encryption scheme for cloud-assisted telemedicine information system" Computers and Electrical Engineering 120: 109816. DOI: 10.1016/j.compeleceng.2024.109816.
- [14] Q. Chai and G. Gong. “Verifiable symmetric search able encryption for semi-honest-but-curious cloud servers”. In: 2012 IEEE international conference on communications (ICC). IEEE. 2012, 917–922. DOI: 10.1109/ ICC.2012.6364125.
- [15] L. Chen, K. Huang, M. Manulis, and V. Sekar, (2021) “Password-authenticated searchable encryption" International Journal of Information Security 20(5): 675–693. DOI: 10.1007/s10207-020-00524-5.
- [16] C. V. Joe and J. S. Raj, (2021) “Deniable authentication encryption for privacy protection using blockchain" Journal of Artificial Intelligence and Capsule Networks 3(3): 259–271. DOI: 10.36548/jaicn.2021.3.008.
- [17] X. Yan, S. Feng, Y. Tang, P. Yin, and D. Deng, (2022) “Blockchain-based verifiable and dynamic multi-keyword ranked searchable encryption scheme in cloud computing" Journal of Information Security and Applications 71: 103353. DOI: 10.1016/j.jisa.2022.103353.
- [18] H. Li, Q. Huang, J. Huang, and W. Susilo, (2022) “Public-key authenticated encryption with keyword search supporting constant trapdoor generation and fast search" IEEE Transactions on Information Forensics and Security 18: 396–410. DOI: 10.1109/TIFS.2022.3224308.
- [19] X. Tang, C. Guo, K.-K. R. Choo, Y. Liu, and L. Li, (2021) “A secure and trustworthy medical record sharing scheme based on searchable encryption and blockchain" Computer Networks 200: 108540. DOI: 10.1016/j.comnet.2021.108540.
- [20] L. Yao, J. Weng, A. Yang, X. Liang, Z. Wu, Z. Jiang, and L. Hou, (2023) “Scalable CCA-secure public-key authenticated encryption with keyword search from ideal lattices in cloud computing" Information Sciences 624: 777–795. DOI: 10.1016/j.ins.2022.12.035.
- [21] L. Teng and H. Li, (2018) “A High-efficiency Discrete Logarithm-based Multi-proxy Blind Signature Scheme via Elliptic Curve and Bilinear Mapping." Int. J. Netw. Se cur. 20(6): 1200–1205. DOI: 10.6633/IJNS.20181120(6).20.
- [22] Y.Sun, S. Yin, J. Liu, and L. Teng, (2019) “A Certificate less Group Authenticated Key Agreement Protocol Based on Dynamic Binary Tree." Int. J. Netw. Secur. 21(5): 843–849. DOI: 10.6633/IJNS.20190921(5).17.
- [23] B.B.Gupta,K.-C. Li, V. C. Leung, K. E. Psannis, S. Ya maguchi, et al., (2021) “Blockchain-assisted secure fine grained searchable encryption for a cloud-based healthcare cyber-physical system" IEEE/CAA Journal of Auto matica Sinica 8(12): 1877–1890. DOI: 10.1109/JAS.2021.1004003.
- [24] J. G. Chamani, Y. Wang, D. Papadopoulos, M. Zhang, and R. Jalili, (2021) “Multi-user dynamic searchable symmetric encryption with corrupted participants" IEEE Transactions on Dependable and Secure Computing 20(1): 114–130. DOI: 10.1109/TDSC.2021.3127546.
- [25] C. Jiang, C. Xu, Z. Zhang, and K. Chen, (2023) “SR PEKS: Subversion-resistant public key encryption with keyword search" IEEE Transactions on Cloud Computing 11(3): 3168–3183. DOI: 10.1109/TCC.2023.3266459.
- [26] F. Shen, L. Shi, J. Zhang, C. Xu, Y. Chen, and Y. He, (2024) “BMSE: Blockchain-based multi-keyword search able encryption for electronic medical records" Computer Standards & Interfaces 89: 103824. DOI: 10.1016/j.csi.2023.103824.
- [27] F. Zhou, Z. Jiao, Q. Wang, and J. Sun, (2024) “Bcvse: Verifiable searchable encryption scheme with blockchain supporting fuzzy query" Arabian Journal for Science and Engineering 49(3): 4401–4418. DOI: 10.1007/s13369-023-08482-5.
- [28] A. Arabnouri and A. Shafieinejad, (2024) “BACASE SH: Blockchain-based authenticated certificate-lessasym metric searchable encryption for smart healthcare" Peer to-Peer Networking and Applications 17(4): 2298–2314. DOI: 10.1007/s12083-024-01687-x.
- [29] H.Yu, S. Liu, L. Chen, and Y. Gao, (2024) “Blockchain enabled one-to-many searchable encryption supporting designated server and multi-keywords for Cloud-IoMT" Journal of Systems Architecture 149: 103103. DOI: 10.1016/j.sysarc.2024.103103.