REFERENCES
- [1]Sperotto, , Schaffrath, G., Sadre, R., Morariu, C., Pras, A., and Stiller, B., “An Overview of IP Flow-Based Intrusion Detection,” IEEE Communications Surveys & Tutorials, Vol. 12, pp. 343-356, 3rd Quarter 2010. Doi:10.1109/SURV.2010.032210.00054
- [2]Anirudh, M., Thileeban, S. A., and Nallathambi, D. J., “Use of Honeypots for Mitigating DoS Attacks Targeted on IoT Networks,” 2017 Int’l Conf. on Computer, Communication and Signal Processing, Jan. 2017. Doi:10.1109/ICCCSP.2017.7944057
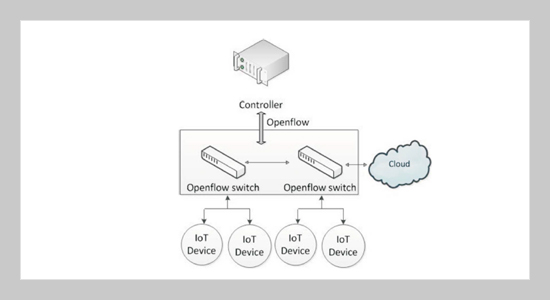
- [3]Bhunia, S. S. and Gurusamy, M., “Dynamic Attack Detection and Mitigation in IoT Using SDN,” 2017 Int’l Telecommunication Networks and Applications Conf., Nov. 2017. Doi:10.1109/ATNAC.2017.8215418
- [4]Kim, E. J., Jun, J. A., and Kim, N.-S., “The Method of Controlling Traffic Paths in IoT-based Software Defined Network,” IEEE 7th Annual Ubiquitous Computing, Electronics & Mobile Communication Conf., Oct. 2016. Doi:10.1109/UEMCON.2016.7777824
- [5]“Argus”[Online], Available:https://qosient.com/argus/.
- [6]“Honeyd” [Online]. Available: http://www.honeyd.org/.
- [7]Meena, G. and Choudhary R. R., “A Review Paper on IDS Classification Using KDD 99 and NSL KDD Dataset in WEKA,” 2017 Int’l Conf. on Computer, Communications and Electronics, July 2017, pp.553-558. Doi : 10.1109/COMPTELIX.2017.8004032
- [8]Mhetre, V. and Nagar, M., “Classification Based Data Mining Algorithms to Predict Slow, Average and Fast Learners in Educational System Using WEKA,” 2017 Int’l Conf. on Computing Methodologies and Communication, July 2017, pp.475-479. Doi:10.1109/ICCMC.2017.8282735
- [9]Abubakar, A. and Pranggono, B., “Machine Learning Based Intrusion Detection System for Software Defined Networks,” Emerging Security Technologies, pp.138-143, Sept. 2017. Doi:1109/EST.2017.8090413
- [10]Boero, L., Marchese, M., and Zappatore, S., “Support Vector Machine Meets Software Defined Networking in IDS Domain,” 29th Int’l Teletraffic Congress, Sept. 2017, pp.25-30. Doi: 10.23919/ITC.2017.8065806
- [11]Dao, N. N., Park, J., Park, M., and Cho, S., “A Feasible Method to Combat against DDoS Attack in SDN Network,” 2015 Int’l Conf. on Information Networking, Jan. 2015, pp. 309-311. Doi: 10.1109/ICOIN.2015.7057902
- [12]Mousavi, S. M. and St-Hilaire, M., “Early Detection of DDoS Attacks against SDN Controllers,” 2015 Int’l Conf. in Computing Networking and Communications, Feb. 2015, pp. 77-81. Doi: 10.1109/ICCNC.2015.7069319
- [13]Buragohain, C. and Medhi, N., “FlowTrApp: An SDN Based Architecture for DDoS Attack Detection and Mitigation in Data Centers,” 3rd Int’l Conf. on Signal Processing and Integrated Networks, Feb. 2016, pp. 519-524. Doi:10.1109/SPIN.2016.7566750
- [14]Gkountis, C., Taha, M., Lloret, J., and Kambourakis, G., “Lightweight Algorithm for Protecting SDN Controller against DDoS Attacks,” 2017 Wireless and Mobile Networking Conference, Sept. 2017.Doi:10.1109/WMNC.2017.8248858
- [15]S. A., Khalid, J., Khayam, S. A., “Revisiting Traffic Anomaly Detection Using Software Defined Networking,” Recent Advances in Intrusion Detection, Vol. 6961, pp. 161-180, 2011. Doi:10.1007/978-3-642-23644-0_9
- [16]Jafarian, J. H., Al-Shaer, E., and Duan, Q., “Openflow Random Host Mutation: Transparent Moving Target Defense Using Software Defined Networking,” 1st Workshop on Hot Topics in Software Defined Networks, Aug. 2012, pp. 127-132.
- [17]Shin, S., Yegneswaran, V., Porras, P., and Gu, G., “AVANT-GUARD: Scalable and Vigilant Switch Flow Management in Software-Defined Networks,” 2013 ACM SIGSAC Conference on Computer & Communications Security, Nov. 2013, pp. 413-424.
- [18]Deogirikar, J. and Vidhate, A., “Security Attacks in IoT: A Survey,” IoT in Social, Mobile, Analytics and Cloud, pp.32-37, Feb. 2017. Doi:10.1109/I-SMAC.2017.8058363
- [19]“Mininet”[Online],Available:http://mininet.org/walkthrough/.
- [20]“Ryu.” [Online]. Available: http://osrg.github.io/ryu/.
- [21]Kolias, C., Kambourakis, G., Stavrou, A., and Voas, J., “DDoS in the IoT: Mirai and Other Botnets,” IEEE Computer, Vol. 50, No. 7, pp. 80-84, July 2017. Doi:10.1109/MC.2017.201
- [22]De Donno, M., Dragoni, N,, Giaretta, A., and Spognardi, A., “Analysis of DDoS-capable IoT Malwares,” 2017 Federated Conf. on Computer Science and Information Systems, Sept. 2017, pp. 807-816. Doi:10.15439/2017F288
- [23]Sforzin, A., Mármol, F. G., Conti, M., and Bohli, J.-M., “RPiDS: Raspberry Pi IDS — A Fruitful Intrusion Detection System for IoT,” 2016 Ubiquitous Intelligence & Computing, Advanced and Trusted Computing, Scalable Computing and Communications, Cloud and Big Data Computing, Internet of People, and Smart World Congress, July 2016, pp.440-448. Doi:10.1109/UIC-ATC-ScalCom-CBDCom-IoP-SmartWorld.2016.0080
- [24]Bhosale, D. A., and Mane, V. M., “Comparative Study and Analysis of Network Intrusion Detection Tools,” 2015 Int’l Conf. on Applied and Theoretical Computing and Communication Technology, Oct. 2015, pp. 312-315. Doi:10.1109/ICATCCT.2015.7456901
- [25]Miettinen, M., Marchal, S., Hafeez, I., Asokan, N., Sadeghi, A.-R., and Tarkoma, S., “IoT Sentinel: Automated Device-Type Identification for Security Enforcement in IoT,” 37th IEEE Int’l Conf. on Distributed Computing Systems, Jun. 2017. Doi:10.1109/ICDCS.2017.283
- [26]Aggarwal, P. and Sharma, S. K., “An Empirical Comparison of Classifiers to Analyze Intrusion Detection,” Advanced Computing & Communication Technologies, pp. 446-450, Feb. 2015. Doi:10.1109/ACCT.2015.59
- [27]Joshi, A., Wazid, M., and Goudar, R. H., “An Efficient Cryptographic Scheme for Text Message Protection Against Brute Force and Cryptanalytic Attacks,” Procedia Computer Science, 48, pp. 360-366, 2015. Doi:10.1016/j.procs.2015.04.194
- [28]Kaynar, K., “A Taxonomy for Attack Graph Generation and Usage in Network Security,” Journal of Information Security and Applications, Vol. 29, pp. 27-56, 2016. Doi:10.1016/j.jisa.2016.02.001