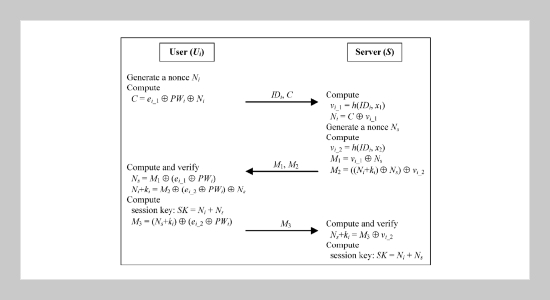
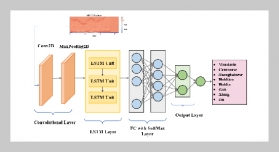
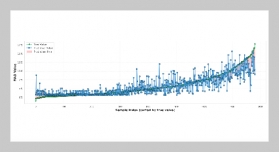
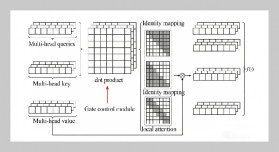
REFERENCES
- [1] M’Raïhi, D. and Yung, M., “E-Commerce Applications of Smart Cards,” Computer Networks, Vol. 36, No. 4, pp. 453�472 (2001). doi: 10.1016/S1389-1286 (01)00166-9
- [2] Lamport, L., “Password Authentication with Insecure Communication,” Communications of the ACM, Vol. 24, No. 11, pp. 770�772 (1981). doi: 10.1145/358790. 358797
- [3] Hwang, M. S. and Li, L. H., “A New Remote User Authentication Scheme Using Smart Cards,” IEEE Transactions on Consumer Electronics, Vol. 46, No. 1, pp. 28�30 (2000). doi: 10.1109/30.826377
- [4] Juang, W. S., “Efficient Password Authenticated Key Agreement Using Smart Cards,” Computers & Security, Vol. 23, No. 2, pp. 167�173 (2004). doi: 10.1016/ j.cose.2003.11.005
- [5] Fan, C. I., Chan, Y. C. and Zhang, Z. K., “Robust Remote Authentication Scheme with Smart Cards,” Computers & Security, Vol. 24, No. 8, pp. 619�628 (2005). doi: 10.1016/j.cose.2005.03.006
- [6] Liaw, H. T., Lin, J. F. and Wu, W. C., “An Efficient and Complete Remote User Authentication Scheme Using Smart Cards,” Mathematical and Computer Modelling, Vol. 44, No. 1�2, pp. 223�228 (2006). doi: 10. 1016/j.mcm.2006.01.015
- [7] Liao, I. E., Lee, C. C. and Hwang, M. S., “A Password Authentication Scheme over Insecure Networks,” Journal of Computer and System Sciences, Vol. 72, No. 4, pp. 727�740 (2006). doi: 10.1016/j.jcss.2005.10.001
- [8] Chung, H. R., Ku, W. C. and Tsaur, M. J., “Weaknesses and Improvement of Wang et al.’s Remote User Password Authentication Scheme for Resource-Limited Environments,” Computer Standards & Interfaces, Vol. 31, No. 4, pp. 863�868 (2009). doi: 10.1016/ j.csi.2008.09.020
- [9] Song, R., “Advanced Smart Card Based Password Authentication Protocol,” Computer Standards & Interfaces, Vol. 32, No. 5�6, pp. 321�325 (2010). doi: 10.1016/j.csi.2010.03.008
- [10] Sun, H. M., “An Efficient Remote User Authentication Scheme Using Smart Cards,” IEEE Transactions on Consumer Electronics, Vol. 46, No. 4, pp. 958�961 (2000). doi: 10.1109/30.920446
- [11] Hwang, M. S., Lee, C. C. and Tang, Y. L., “A Simple Remote User Authentication Scheme,” Mathematical and Computer Modelling, Vol. 36, No. 1�2, pp. 103� 107 (2002). doi: 10.1016/S0895-7177(02)00106-1
- [12] Chien, H. Y., Jan, J. K. and Tseng, Y. M., “An Efficient and Practical Solution to Remote Authentication: Smart Card,” Computers & Security, Vol. 21, No. 4, pp. 372� 375 (2002). doi: 10.1016/S0167-4048(02)00415-7
- [13] Ku, W. C. and Chen, S. M., “Weaknesses and Improvements of an Efficient Password Based Remote User authentication Scheme Using Smart Cards,” IEEE Transactions on Consumer Electronics, Vol. 50, No. 1, pp. 204�207 (2004). doi: 10.1109/TCE.2004.1277863
- [14] Shieh, W. G. and Wang, J. M., “Efficient Remote Mutual Authentication and Key Agreement,” Computers & Security, Vol. 25, No. 1, pp. 72�77 (2006). doi: 10.1016/j.cose.2005.09.008
- [15] Shieh, W. G. and Horng, W. B., “An Improvement of Liaw-Lin-Wu’s Efficient and Complete Remote Mutual Authentication with Smart Cards,” WSEAS Transactions on Information Science and Applications, Vol. 4, No. 6, pp. 1200�1205 (2007).
- [16] Huang, H. F. and Wei, W. C., “A New Efficient and Complete Remote User Authentication Protocol with Smart Card,” International Journal of Innovative Computing, Information and Control, Vol. 4, No. 11, pp. 2803�2808 (2008).
- [17] Yeh, K. H., Lo, N. W. and Winata, E., “Cryptanalysis of an Efficient Remote User Authentication Scheme with Smart Cards,” International Journal of Innovative Computing, Information and Control, Vol. 6, No. 6, pp. 2595�2608 (2010).